I wanted to get this quick-read out there, as I recently ran into this issue and didn’t see any articles about a remedy for it.
Here’s some background: I’ve set up an NPS server in Azure for a client so they can leverage the NPS MFA extension that you can integrate into your Azure AD MFA component. We got the NPS with no issue, but as soon as we installed the NPS extension and created the cert, our test connection would instantly fail.
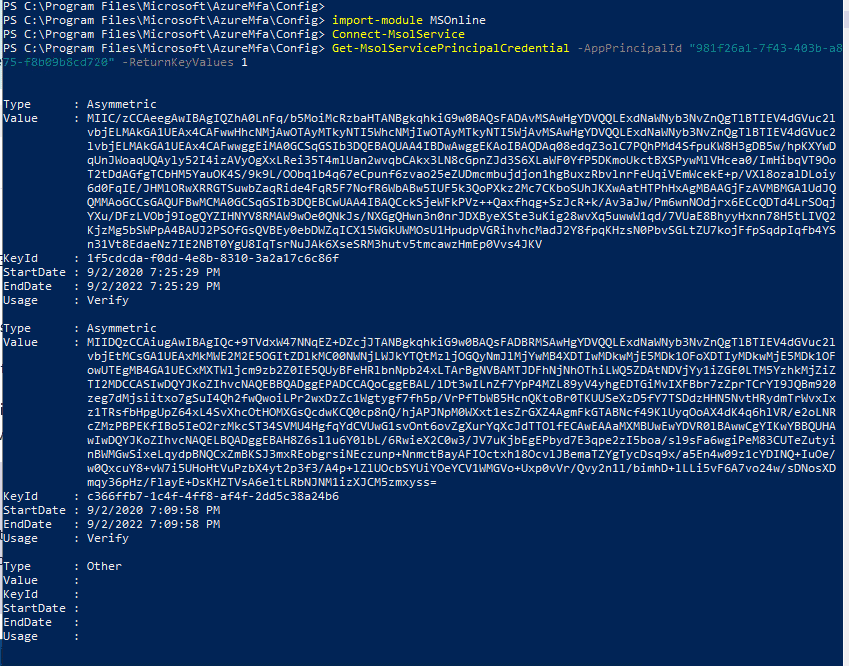
All I saw in the NPS was the “extension was being bypassed.” It was frustrating, to say the least. However, while troubleshooting, I noticed I had multiple certificates, but no way to remove. (Note the following commands are run to get the certificate properties):
import-module MSOnline
Connect-MsolService
Get-MsolServicePrincipalCredential -AppPrincipalId “981f26a1-7f43-403b-a875-f8b09b8cd720” -ReturnKeyValues 1 )
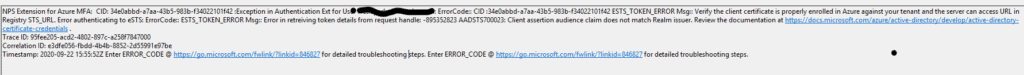
I also saw this error in event viewer logs under Applications and Services: Logs>Microsoft>AzureMfa>AuthZ:
NPS Extension for Azure MFA: CID: 34e0abbd-a7aa-43b5-983b-f34022101f42 :Exception in Authentication Ext for User [email protected] :: ErrorCode:: CID :34e0abbd-a7aa-43b5-983b-f34022101f42 ESTS_TOKEN_ERROR Msg:: Verify the client certificate is properly enrolled in Azure against your tenant and the server can access URL in Registry STS_URL. Error authenticating to eSTS: ErrorCode:: ESTS_TOKEN_ERROR Msg:: Error in retreiving token details from request handle: -895352823 AADSTS700023: Client assertion audience claim does not match Realm issuer. Review the documentation at https://docs.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials .
Trace ID: 95fee205-acd2-4802-897c-a258f7847000
Correlation ID: e3dfe056-fbdd-4b4b-8852-2d55991e97be
Timestamp: 2020-09-22 15:55:52Z Enter ERROR_CODE @ https://go.microsoft.com/fwlink/?linkid=846827 for detailed troubleshooting steps. Enter ERROR_CODE @ https://go.microsoft.com/fwlink/?linkid=846827 for detailed troubleshooting steps.
I spoke with the Microsoft MFA team, who was awesome by the way, and he reviewed the certificate with me and came to the same conclusion: we needed to remove the certificates and only have one. Which leads me to the following PowerShell script that needs to be run once you are signed in to your Azure tenant:
Remove-MsolServicePrincipalCredential -AppPrincipalId “981f26a1-7f43-403b-a875-f8b09b8cd720” -KeyIds 98622eb8-eca4-4a3a-8458-b6cc9d766033
AppPrincipalId is the App ID for the MFA Auth, so that will be the same for you. However, KeyIds will be different and is located in the Azure AD certificate properties mentioned in Fig 1.1 in today’s article.

The rep said we could just remove all but the most current time-stamped certificate property; however, I just started from scratch. I removed all certificates (including the Azure AD tenant certificate created on the NPS server) and uninstalled the NPS extension. Once my reboot was completed, I installed the extension and created the new certificate. Once we confirmed certificate properties in Azure AD matched, we had our network engineer test. Without hesitation, the NPS responded, MFA prompt initiated, and there were smiles all around!

